During a recent penetration test I came up against a security feature that would invalidate my session whilst I was fuzzing if it saw simple attack strings, so if I used <script> anywhere then it’d kill my session. Most frustrating! Especially as it essentially prevented the use of tools such as Burp’s Active Scanner and it made using Repeater inconvenient too. So I quickly threw together a Burp Macro to handle automatic re-authentication for me and went back to fuzzing!
So here’s how to do that!
Macros can be used for a few things, such as automatically extracting CSRF tokens from a page and including them in scanner requests, in this case I’m going to demo their functionality and set up with a macro that will detect if our session has become invalidated and revalidate it automatically.
First of all the Session Handling for Burp is found under Options > Sessions and it looks like this:
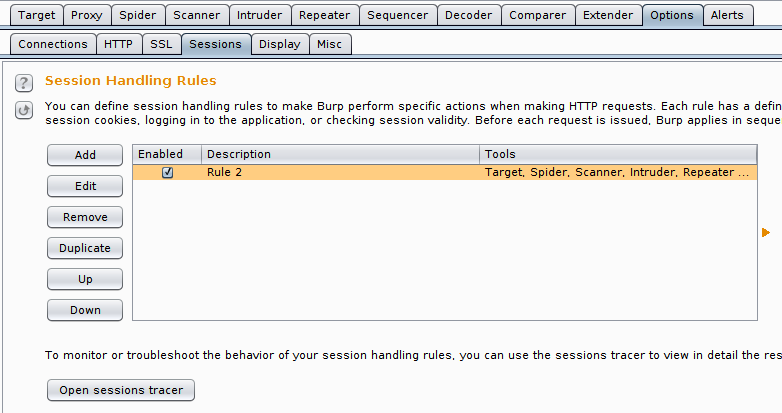
You can go ahead and hit Add here, which will allow you to define a new rule. The menu looks like this:
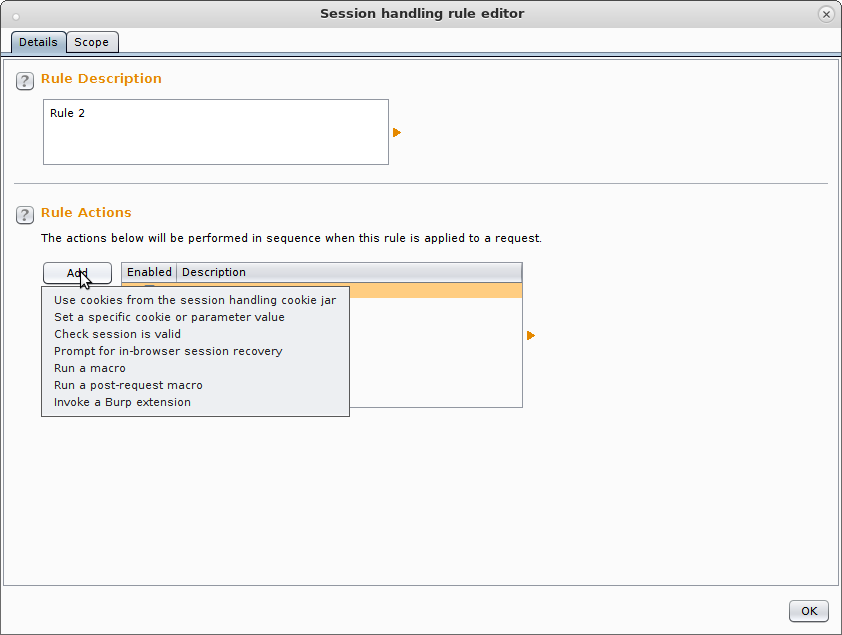
So each rule has a “Scope”, “Description” and “Action”. Description is an easy one and you should just add in here what the rule is for. Rules have their own specific scopes, so you can either inform it to operate on all pages, the same scope as you set up within the Target tab or a custom scope for this rule. That’s all handled under the “Scope” tab.
The main work is done under “Action” though, which is shown above and for automatic re-authentication you’ve got a couple of options, you can either “Run a macro” which is good if you want to re-authenticate after every single request (so you know your session is clean when you fuzz) or you can re-authenticate only whenever the session becomes invalidated (which is a touch more efficient!).
We’ll go with the second one here, because I think it’s the one most people will want, but the set up process is almost identical. So you can go ahead and hit Add > “Check session is valid”
That’ll show this menu:
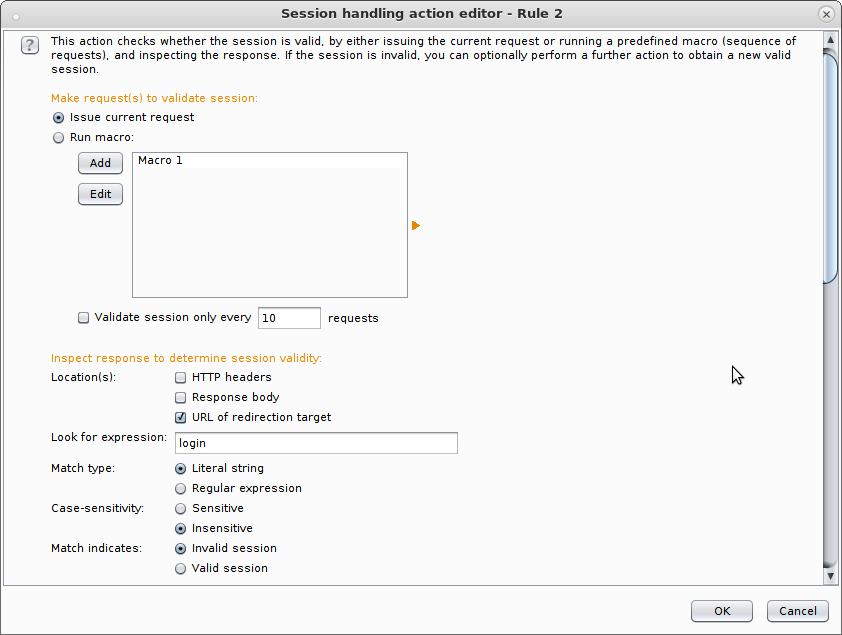
As you can see from the scroll bar this menu is quite long, but there’s really only two parts to it: “How do we check if the session is valid?” and “What do we do if it’s invalid?”. The first one is shown above. So in this simple example I need to check if the request resulted in a HTTP 401 and if it did then I know I’ve been invalidated. You can go ahead and replace this with the text from whatever error message you see when you’ve been logged out. So I simply select “Issue current request” followed by “Response body” and fill in “401 – Unauthorized” in the box that says “Look for expression”.
That’s it! If you my response body contains that string then it’s likely I’ve been invalidated and I need to re-authentication, simple! So just scroll down and we can tell Burp how to re-authenticate. That part of the menu looks like this:
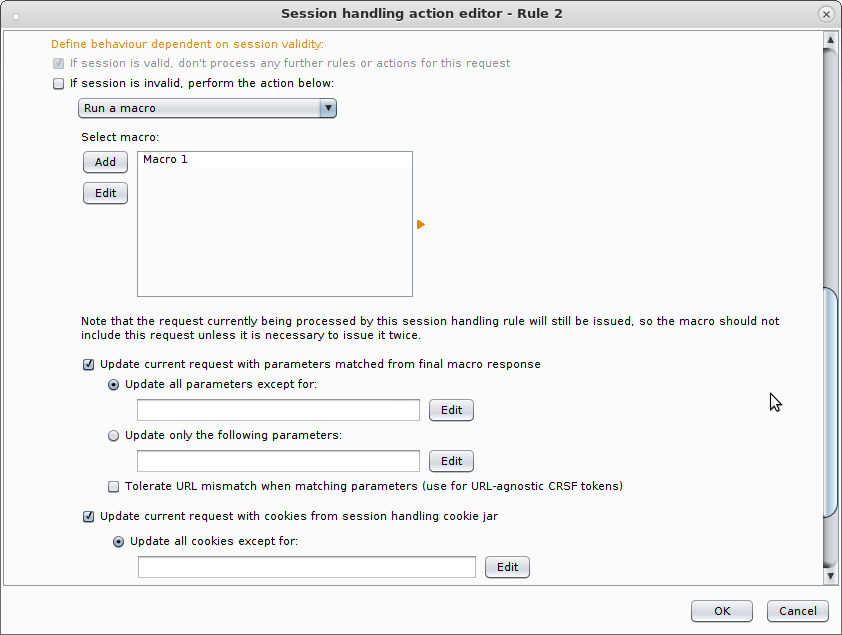
So I select “If session is invalid, perform the action below:” and “Update current request with cookies from session handling cookie jar”. So that if I’m dropped I add the new cookies and I’m back in. So the perform action bit then, is simply a macro that issues a few requests and essentially gets a new cookie. I used a macro here, so his “Add” and you’re prompted with a big menu that looks like this:
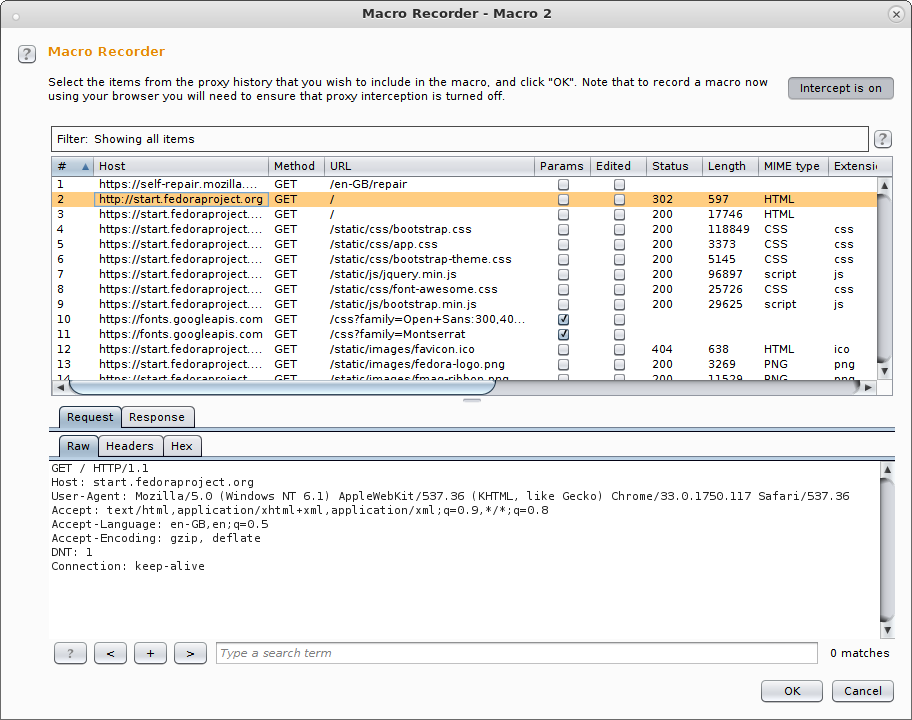
Now burp is tracking all of the steps you take in your web browser, so you can simply perform a logout followed by a log in and it’ll learn how that process works. Then click and drag to highlight the right requests involved in that process and hit the okay button (found at the bottom of the same window but not shown in the screenshot). Burp will then show you the macro that you’ve recorded and let you test it out!
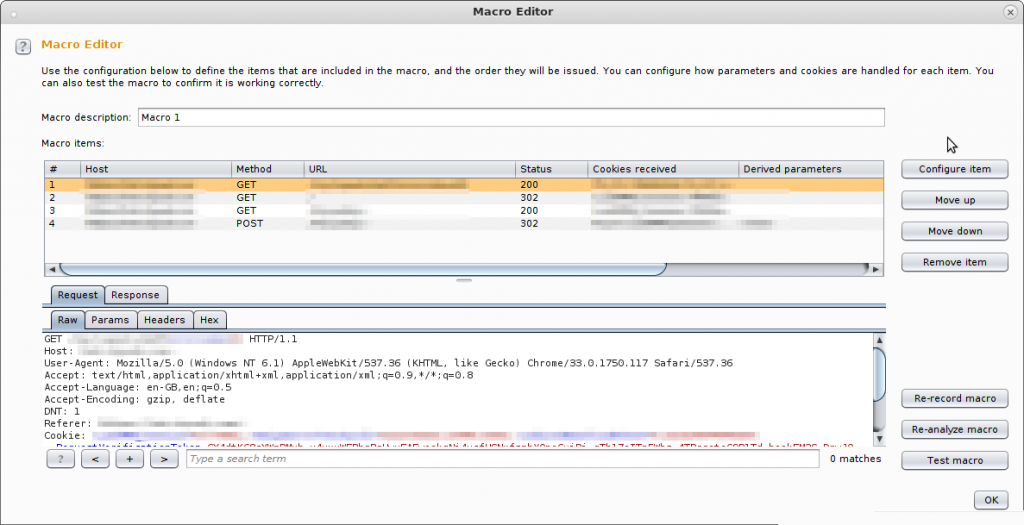
So here’s my Macro, the first request logs me out and then the next three are how this application sets up a new session through a new login attempt but you can see here you’ve got the option to test the macro (and if it doesn’t work you can re-record it.) but if you go ahead and hit okay – you’re done!
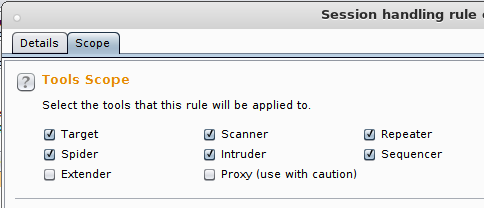
By default the session test will run for all tools other than the proxy itself (so it works with repeater, intruder, scanner, etc) but you can configure that on the “Scope” tab I mentioned earlier:
It all works transparently in the background whenever these tools run, which is great because it lets you get on with the job at hand – however if things aren’t working quite right it can be a touch difficult to debug, so I’d recommend you go ahead and install the Logger++ extension now so that you can track all the requests made by scanner and see if your macros and scans are running as they should, that’s available here: Logger++!